Understanding SAML: The Backbone of Secure Identity Federation
In today’s digital landscape, providing seamless and secure access to multiple applications is essential. Single Sign-On (SSO) serves as the gateway to this convenience by allowing users to authenticate once and gain access to a variety of services without re-entering credentials. SAML, a protocol designed for secure identity federation, plays a crucial role in realizing the promise of SSO.
The Role of SAML in SSO
At its core, SAML is an XML-based standard that governs the exchange of authentication and authorization data between two parties: the Identity Provider (IdP) and the Service Provider (SP). This exchange makes SSO possible by ensuring that once a user is authenticated, the confirmation of that authentication - known as an assertion - is securely passed along to every connected service.
Key Benefits of SSO with SAML
- Improved User Experience: A single point of entry for multiple applications means fewer passwords to remember and manage.
- Centralized Authentication: IT teams can enforce consistent security policies by managing authentication centrally.
- Enhanced Security: Limiting the number of times credentials are transmitted reduces the risk of interception and phishing attacks.
- Streamlined Administration: Simplified user management and automated provisioning make it easier to control access rights across the organization.
How SAML Works
SAML facilitates the secure transmission of user credentials and attributes through a series of well-defined messages. A typical process unfolds as follows:
- User Requests Access: A user attempts to access a protected resource on a service provider.
- Authentication Request: The service provider redirects the user to the identity provider with an authentication request.
- User Authentication: The identity provider verifies the user using methods such as passwords or multi-factor authentication.
- Assertion Issuance: Upon successful authentication, the identity provider creates a digitally signed XML document—the SAML assertion—that contains the user’s identity information and attributes.
- Response and Access: The assertion is sent back to the service provider, which verifies the signature and grants the appropriate level of access.
For a deeper technical dive into SAML, you can consult the OASIS SAML 2.0 Specification.
Components of a SAML Transaction
The SAML protocol is built around several key components that work together to secure identity federation:
- Identity Provider (IdP): The authority responsible for authenticating users and issuing SAML assertions.
- Service Provider (SP): The application or service that consumes the SAML assertion to grant user access.
- Assertions: The core messages containing details about user authentication, attributes, and authorization decisions.
- Protocols and Bindings: These define how SAML messages are transmitted between the IdP and SP, typically using HTTP POST or HTTP Redirect.
- Profiles: Specific guidelines that dictate how SAML assertions are applied in various scenarios to ensure interoperability across different systems.
Visualizing a SAML Flow
To better understand the process, consider the following diagram that outlines a typical SAML SSO flow:
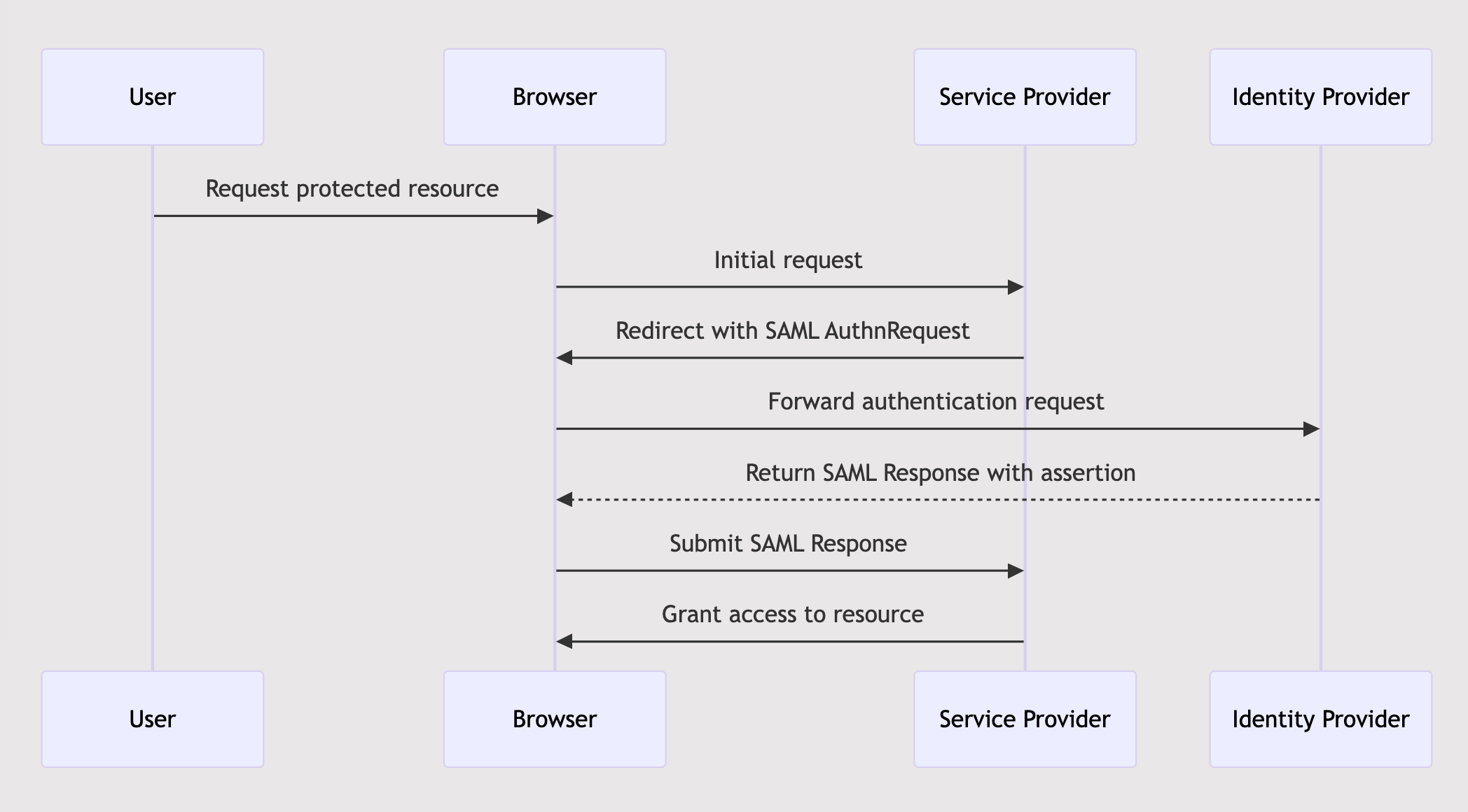
Real-World Applications
SAML is widely adopted across various sectors to enable secure and efficient access:
- Enterprise Applications: Large organizations often use SAML for internal SSO, enabling employees to access a suite of applications with one login.
- Cloud Services: Cloud providers integrate SAML to allow organizations to use their existing identity management systems for secure access to cloud resources.
- Partner Integrations: Businesses working with external partners employ SAML to establish trusted relationships, ensuring secure data sharing without compromising system security.
Some History
SAML was developed in the early 2000s. The first version, SAML 1.0, emerged around 2002, followed by an incremental update with SAML 1.1 in 2003. However, it was the release of SAML 2.0 in 2005—a major update that introduced significant improvements and enhancements—that truly set the stage for widespread adoption. With the finalized SAML 2.0 specification, enterprises found a robust, flexible, and secure framework for implementing Single Sign-On (SSO) and federated identity management. As organizations increasingly shifted towards web-based and cloud services, SAML 2.0 quickly became the de facto standard for secure access management.
Conclusion
SAML is much more than a protocol—it is a foundational element that empowers SSO, streamlining access, enhancing security, and simplifying user management. By securely transmitting authentication data between identity providers and service providers, SAML plays a pivotal role in modern digital ecosystems. For IT professionals and business leaders alike, understanding and leveraging SAML is key to building robust, user-friendly access management systems.
For further technical details and best practices, revisiting the OASIS SAML 2.0 Specification is highly recommended, and resources like Okta’s knowledge base offer additional insights and real-world case studies.
Posts in this series
- Streamlining Access: The Power of Single Sign-On (SSO)
- OpenID Connect Demystified: Modernizing Authentication
- OAuth 2.0 Explained: The Modern Authorization Framework
- Understanding SAML: The Backbone of Secure Identity Federation